Web application penetration testing from CREST certified testers
- Secure vital customer facing and internal web applications from cyber threats
- Understand how a future successful attack could impact business operations
- Assure stakeholders, third-party suppliers, and customers that your web applications are secure
- If you need to reschedule we will not charge a penalty fee
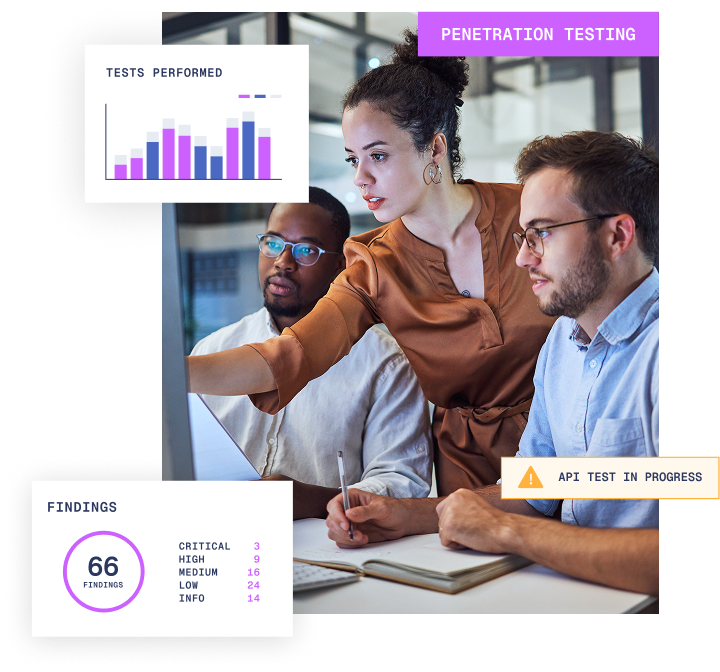
Get a faster, clearer, and simpler view of your web app vulnerabilities
Web applications handle large amounts of data and underpin almost every business function. As a result, they are a common targets for cyber criminals.
Our web application penetration testing simulates a skilled attacker executing a campaign against your customer facing or internal web apps and APIs to find exploitable vulnerabilities and insecure configurations before they can be discovered and exploited for real.
Book your web app pen test scoping call
Ready to get a faster, clearer, and simpler view of your web application security?
Whether you need help or a quote for a live project or just some quick advice, our team of cybersecurity experts here for you. Simply complete the form, or give us a call on 0330 460 4633 to start a conversation.
Trusted to provide a faster, clearer, and simpler view of cybersecurity by
What is involved in web application penetration testing?
Our CREST certified penetration testers conducts manual and automated security assessments to simulate real-world attacks, while ensuring not to impact day-to-day operations.
Our Comprehensive Approach: SAST & DAST
- SAST (Static Application Security Testing) analyses source code for vulnerabilities like SQL injection and cross-site scripting early in development.
- DAST (Dynamic Application Security testing) simulates real-world attacks on running applications, uncovering security weaknesses that only emerge under certain conditions.
By combining SAST and DAST testing we provide a holistic view of an application’s security, covering both code-level and runtime vulnerabilities for robust protection.
Authentication & Authorisation
Evaluate login mechanisms, session management, and privilege escalation risks to ensure users only access what they are permitted to.
File Upload Handling
Inspect upload functionality for malicious file execution risks, MIME-type mismatches, and unrestricted file access.
Input Validation
Identify injection points including SQL, XSS, and command injection through improper sanitization of user-controlled inputs.
Transport Layer Protection
Verify secure configuration of HTTPS, TLS settings, and encryption enforcement to prevent data interception or manipulation.
Error Handling & Information Leakage
Test how your app responds to unexpected input and failures, ensuring no sensitive details are disclosed through stack traces or verbose errors.
Security Misconfigurations
Identify common platform misconfigurations including exposed admin panels, default credentials, or unnecessary services.
Patch Management & Dependency Risks
Evaluate use of outdated libraries, CMS components, and third-party tools with known CVEs.
What you can expect from Vambrace web application penetration testing

CREST certified penetration testers
We use CREST certified professionals who bring extensive experience from across multiple sectors ensuring fast, accurate results.
Supported by our Aegis platform
Results from all pen testing activities are integrated into our Aegis risk management platform, automatically creating actionable and tracked task lists, prioritised by the most significant vulnerabilities, and aligned to your bespoke GRC requirements.

Access to immediate in-test reporting
No waiting for your final report. Our real-time reporting gives you live visibility of all findings as soon as they are submitted so you can start fixing critical issues fast. Post-test remediation checks ensure these vulnerabilities have been resolved.
A partner that is flexible to do business with
We get it. Businesses are busy, complex places, so if you need to move a start date, we will not charge a penalty fee.
Benefits of web application penetration testing
Strengthen your organisations’ security posture
Early detection of vulnerabilities prevents data breaches, financial loss, and service disruption.
Having a trusted third party independently assess your web applications is also an invaluable training and continuous improvement tool for internal teams as it:
- Provides actionable recommendations to fix vulnerabilities and improve security practices.
- Helps teams adopt better security controls, patch management, and monitoring practices.
- Also targets web servers, surfacing outdated software, vulnerabilities, and misconfigurations.

Protect against inherent web app security flaws
It is not uncommon to uncover vulnerabilities in widely used ‘off the shelf’ commercial applications.
Default configurations: Commercial or open-source applications arrive with default settings that may have not been changed or updated by the end user.
Third-party dependencies: Commercial applications often rely on libraries or plugins, which may contain outdated or unpatched vulnerabilities.
The price of being popular: Well known software will naturally attract more attention from attackers. Publicly disclosed vulnerabilities in widely used apps like CMS platforms are often communicated and exploited quickly.

Increase customer confidence
Customers will feel reassured knowing that your web applications have undergone rigorous testing to identify and fix vulnerabilities.
Documented evidence of security testing is either required or strongly recommended for most major security standards, especially when applications handle personal data, financial transactions, or critical business operations. Use our Aegis platform to store and easily share all your pen testing reports with your stakeholders.
- Having prepared documentation always available for inspection can significantly reduce deal closure and audit timelines.
- Web application penetration testing will help meet regulatory obligations against:
- PCI DSS
- ISO 27001
- GDPR
- HIPPA
- NIST Standards
- SOC 2
Web application penetration testing FAQs
Web application penetration testing is a simulated, controlled cyberattack on your web application to identify vulnerabilities, misconfigurations, and insecure functionality before malicious hackers can exploit them. It helps improve your application’s security posture and protect sensitive data.
Even well-developed applications can have hidden vulnerabilities. Web application penetration testing exposes weaknesses in authentication, input handling, business logic, APIs, and server configuration, helping prevent data breaches, financial loss, and reputational damage.
- After any major feature releases or updates.
- At least once a year for ongoing security assurance.
- Whenever regulatory compliance requires it.
In a vast majority of cases, yes. Testers coordinate in advance with teams to define safe boundaries and critical areas that must remain fully operational. Tests also focus on simulated attacks, vulnerability scanning, and non-destructive checks that do not disrupt normal day-to-day functionality or usability. Your users and internal teams won’t notice web application testing activity.
The duration depends on the application’s size, complexity, and scope of testing. A small application may take a couple of days, while large enterprise systems can take several weeks. A clear timeline is always provided before testing begins.






