Mobile app penetration testing from CREST certified testers
- Uncover vulnerabilities or misconfigurations in Android, iOS, and cross-platform apps
- Understand how a future successful attack could impact business operations
- Assure stakeholders, third-parties, and customers that your mobile applications are secure
- If you need to reschedule we will not charge a penalty fee
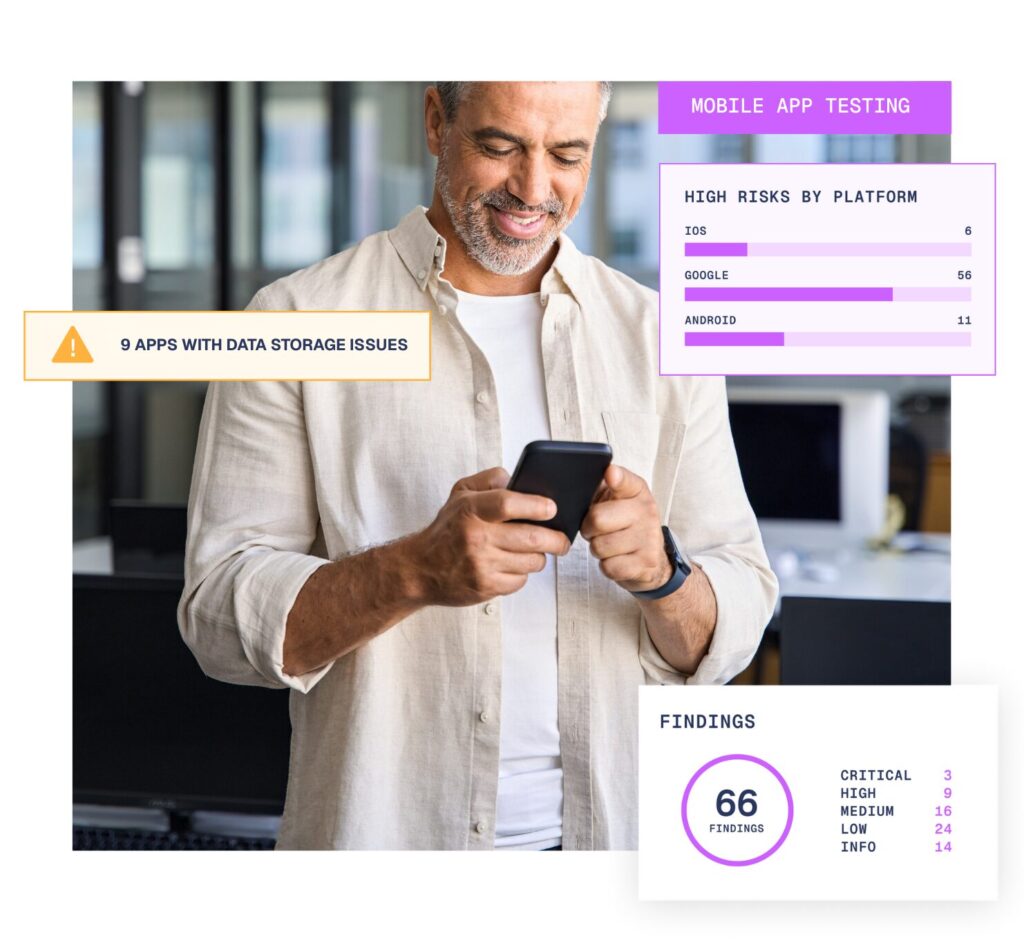
Get a faster, clearer, and simpler view of your mobile application vulnerabilities
Mobile applications are critical for enabling seamless communication and transactions with customers. They handle large amounts of data and underpin day-to-day operations. As a result, they are a common targets for cyber criminals.
We deploy advanced testing techniques on iOS and Android apps that simulate real-world attack scenarios, uncovering weaknesses before they can be exploited. Whether your mobile application is in development or already deployed, our penetration testers will surface issues like API misconfigurations, insecure data storage, and authentication weaknesses to enhance your existing security measures.
Book your mobile app pen test scoping call
Ready to get a faster, clearer, and simpler view of your mobile app security?
Whether you need help or a quote for a live project or just some quick advice, our team of cybersecurity experts here for you. Simply complete the form, or give us a call on 0330 460 4633 to start a conversation.
Trusted to provide a faster, clearer, and simpler view of cybersecurity by
What is involved in mobile app penetration testing?
Our CREST certified penetration testers conduct manual and automated security assessments to simulate real-world attacks, while ensuring not to impact day-to-day operations.
SAST & DAST: Our comprehensive approach to mobile app penetration testing
- SAST (Static Application Security Testing) Review your application’s source code to identify potential security flaws at the code level, ensuring vulnerabilities are mitigated before deployment.
- DAST (Dynamic Application Security testing) simulates real-world attacks on running applications, uncovering security weaknesses that only emerge under certain conditions.
By combining SAST and DAST testing we provide a holistic view of an application’s security, covering both code-level and runtime vulnerabilities for robust protection.
Authentication and Session Management
Mobile apps often use access tokens, biometric logins, or third-party identity providers. We assess how credentials are stored and managed, test session timeouts and simulate bypasses such as deep link manipulation or forced browsing.
Insecure Data Storage
We examine local databases, shared preferences, caches, and file system areas to uncover any sensitive information stored without encryption or proper protection, especially in rooted or jailbroken environments.
API Communication & Transport Security
We analyse how your app communicates with backend services, verifying TLS enforcement, certificate validation, and resistance to man-in-the-middle attacks on both public and private APIs.
Reverse Engineering and Code Tampering
It is important to test your app’s resilience against reverse engineering, dynamic instrumentation, and repackaging, including tamper detection mechanisms.
Platform Misconfigurations
Each mobile OS has unique configuration settings that affect security. We look for exported components, insecure intent schemes, over-privileged permissions, and debug or logging settings left enabled in production.
Third-Party Libraries & SDK Risks
Apps often rely on external SDKs for analytics, advertising, or payment processing. We review these components for known vulnerabilities, excessive permissions, privacy violations, and insecure integration practices.
What you can expect from Vambrace mobile app penetration testing

CREST certified penetration testers
We use CREST certified professionals who bring extensive experience from across multiple sectors ensuring fast, accurate results.
Supported by our Aegis platform
Results from all pen testing activities are integrated into our Aegis risk management platform, automatically creating actionable and tracked task lists, prioritised by the most significant vulnerabilities, and aligned to your bespoke GRC requirements.

Access to immediate in-test reporting
No waiting for your final report. Our real-time reporting gives you live visibility of all findings as soon as they are submitted so you can start fixing critical issues fast. Post-test remediation checks ensure these vulnerabilities have been resolved.
A partner that is flexible to do business with
We get it. Businesses are busy, complex places, so if you need to move a start date, we will not charge a penalty fee.
Benefits of mobile app penetration testing
Strengthen your organisations’ security posture
Early detection of vulnerabilities prevents data breaches, financial loss, and service disruption.
Having a trusted third party independently assess your mobile applications is also an invaluable training and continuous improvement tool for internal teams as it:
- Provides actionable recommendations to fix vulnerabilities and improve security practices.
- Helps teams adopt better security controls, patch management, and monitoring practices.
- Evaluates the security of API’s that mobile apps communicate with, ensuring data exchanges are not exposed.

Get assurance that new mobile apps are safe to launch
Test. Test. Test. For organisations trusted to safeguard sensitive data and maintain regulatory compliance, testing new mobile apps is not optional, it’s essential
Test your authentication protocols: Many organisations are starting to introduce authentication beyond username and passwords, and mobile apps now often utilise biometrics and multi-factor authentication. While convenient, like any new features these require thorough testing due to the expanding attack surface and increased risks if weak logic allows attackers to bypass controls and access sensitive features or data.
Test your communication paths: A new app will need to transmit its data to a server. Failure to secure these communication channels with encryption exposes data to interception by attackers, especially over insecure networks. Penetration testing verifies that all communication channels are secure and that sensitive data is encrypted end-to-end.
Test your supply chain: New applications are rarely built from scratch. They utilise a plethora of third-party libraries and existing frameworks to save time. Thorough testing of the supply chain ensures these third-party components are up-to-date and securely implemented, reducing the risk of shipping an insecure app with inherited weaknesses to customers.

Increase customer confidence
Customers will feel reassured knowing that your mobile applications have undergone rigorous testing to identify and fix vulnerabilities.
Documented evidence of mobile app penetration testing is either required or strongly recommended for most major security standards, especially when applications handle personal data or financial transactions. Use our Aegis platform to store and easily share all your pen testing reports with your stakeholders.
- Having prepared documentation always available for inspection can significantly reduce deal closure and audit timelines.
- Mobile app penetration testing will help meet regulatory obligations against:
- PCI DSS
- ISO 27001
- GDPR
- NIST Standards
- SOC 2
Mobile app penetration testing FAQs
Mobile app penetration testing identifies vulnerabilities in iOS and Android apps before attackers can exploit them. During the test, security specialists analyse how the app stores data, communicates with servers, handles authentication, and interacts with the device’s operating system. This process helps uncover risks such as insecure APIs, weak encryption, poor session management, and data exposure. The goal is to provide clear, actionable recommendations that improve the app’s overall security and protect user data.
Yes. Mobile applications on Android and iOS can be penetration tested at the same time, and many organisations choose to assess both platforms in a single engagement. Although the platforms differ in architecture, permissions, and security controls, our testers run parallel workflows to evaluate each app’s behaviour, storage methods, network communication, and API interactions. Testing both versions together provides a complete picture of your mobile security posture, ensures consistent protection across platforms, and often reduces overall project time and cost.
Most organisations will benefit from testing their mobile applications at least once per year, or whenever major updates, new features, or architectural changes are released. Regular penetration testing ensures that new code, third-party libraries, and backend services do not introduce security gaps over time. Apps that handle sensitive data such as financial or medical records should follow a more frequent schedule to maintain strong and continuous security.
In a vast majority of cases, Yes. Testing is typically performed in a controlled staging or test environment to avoid affecting real users or production data. If production testing is required, it is conducted carefully within a predefined scope to ensure the app remains available and stable. Our testers follow strict rules of engagement to ensure your app, data, and users remain safe throughout the assessment.
The duration depends on the application’s size, complexity, and scope of testing. A small app may take a couple of days, while large enterprise systems can take several weeks. We will always provide a clear timeline before mobile app penetration testing begins, but as a guide:
- Small mobile apps: 2-3 days
- Medium mobile apps: 5-10 days
- Larger mobile apps: 10 days+






