External infrastructure penetration testing from CREST certified testers
- Continuously test the foundations of your IT environment: servers, firewalls, VPN’s, DNS, and cloud endpoints
- Understand how a future successful attack could impact business operations
- Process and categorise new and emerging threats at machine speed
- If you need to reschedule we will not charge a penalty fee
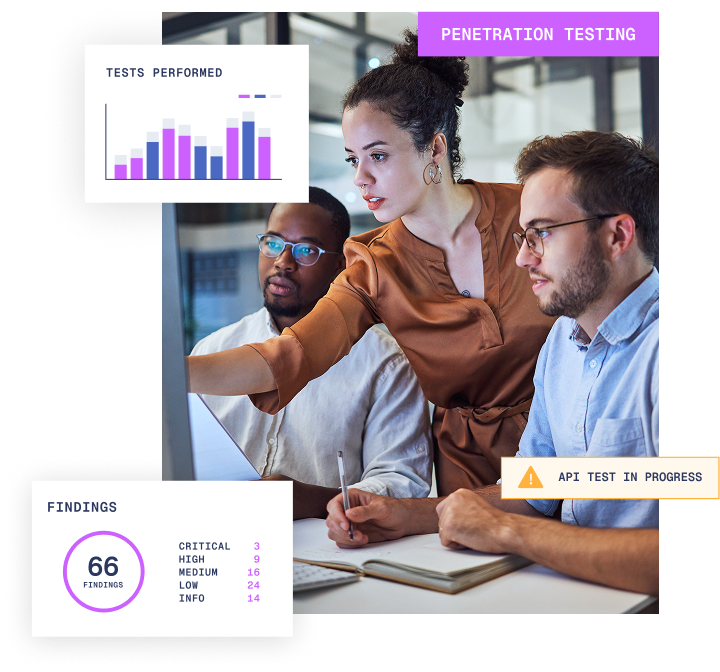
Get a faster, clearer, and simpler view of your external infrastructure vulnerabilities
Your perimeter (firewalls, routers, VPN gateways and web servers) is what separates your internal network from the public internet. These assets come under regular scrutiny by attackers probing defences and looking for misconfigurations, weak encryption, or default credentials.
While mistakes can happen, continuous external infrastructure penetration testing is the best way to quickly surface them to ensure your external attack surface remains resilient and well protected.
Book your pen test scoping call
Ready to get a faster, clearer, and simpler view of your external infrastructure security?
Whether you need help or a quote for a live project or just some quick advice, our team of cybersecurity experts here for you. Simply complete the form, or give us a call on 0330 460 4633 to start a conversation.
Trusted to provide a faster, clearer, and simpler view of cybersecurity by
What is involved in an external infrastructure pen test?
Our CREST certified penetration testers conducts manual and automated security assessments to simulate real-world attacks, while ensuring not to impact day-to-day operations.
Our Comprehensive Approach: Exposure Analysis & Active Exploitation
- Exposure analysis maps your public IP ranges, DNS records and cloud endpoints to identify exposed services. This includes checking firewall rules, VPN gateways, remote management interfaces and public cloud configurations.
- Active exploitation is where we attempt controlled, human-led exploits against identified targets, testing for vulnerabilities such as misconfigured firewalls, unpatched services, weak TLS settings and default credentials to confirm real-world risk.
Combining exposure analysis with active exploitation testing provides a thorough understanding of your external attack surface, covering both visibility and exploitability.
Network Reconnaissance & Enumeration
Gather information on IP ranges, open ports, DNS entries and service banners to build an accurate map of your external footprint.
Perimeter Firewall & VPN Testing
Verify rule sets, ACLs and VPN configurations to ensure only intended traffic is allowed into your network.
Web & Application Server Hardening
Test internet-facing servers for missing patches, directory listing, default credentials and insecure service configurations.
Network Services & Protocol Analysis
Examine services such as SSH, RDP, SMB, SNMP and DNS for weak authentication, exposure of sensitive information and susceptibility to known exploits.
Cloud Endpoint & API Exposure
Assess public cloud services like load balancers, storage buckets and management APIs for misconfigurations that could leak data or grant unauthorized access.
Wireless & Remote Access Security
Evaluate secure configuration of wireless gateways, VPN concentrators and remote desktop gateways to prevent credential theft and unauthorized entry.
What you can expect from our external infrastructure penetration testing

CREST certified penetration testers
We use CREST certified professionals who bring extensive experience from across multiple sectors ensuring fast, accurate results.
Supported by our Aegis platform
Results from all pen testing activities are integrated into our Aegis risk management platform, automatically creating actionable and tracked task lists, prioritised by the most significant vulnerabilities, and aligned to your bespoke GRC requirements.

Access to immediate in-test reporting
No waiting for your final report. Our real-time reporting gives you live visibility of all findings as soon as they are submitted so you can start fixing critical issues fast. Post-test remediation checks ensure these vulnerabilities have been resolved.
A partner that is flexible to do business with
We get it. Businesses are busy, complex places, so if you need to move a start date, we will not charge a penalty fee.
Benefits of external infrastructure penetration testing
Strengthen your organisations’ security posture
Early detection of errors and vulnerabilities prevents data breaches, financial loss, and service disruption.
Having a trusted third party assess your external infrastructure is also an invaluable training and continuous improvement tool for internal teams as it:
- Provides actionable recommendations to fix vulnerabilities and improve security practices.
- Helps teams adopt better security controls, patch management, and monitoring practices.
- Validates if networks are segmented securely into subnetworks to protect critical business assets.

Validates your security controls
Evaluate the effectiveness of the security measures you have implemented
By simulating real-world attacks, we ascertain how and if your access controls and monitoring systems will work under these conditions.
This will include your:
- Firewalls
- Identity and access management
- Intrusion detection and prevention systems
- Encryption levels
- Patch management programs
Increase customer confidence
Customers will feel reassured knowing that your perimeter defences have undergone continuous, controlled, and expert testing to identify and fix vulnerabilities.
Documented evidence of security testing on IT infrastructure is either mandated or strongly recommended by most major security standards, especially when an organisation handles personal data or financial transactions. Having prepared documentation always available for inspection can significantly reduce deal closure and audit timelines.
External infrastructure penetration testing will help meet regulatory obligations against:
- PCI DSS
- ISO 27001
- GDPR
- SOC 2
External Infrastructure Penetration Testing FAQs
It is an ongoing security testing service that simulates real-world attacks on your public-facing systems like web servers, VPNs, firewalls, and cloud endpoints to identify vulnerabilities before attackers can exploit them. Unlike one-time assessments, continuous testing provides regular insights into your security posture.
The external threat landscape evolves rapidly, with new vulnerabilities and attack methods emerging daily legacy periodic assessments are no longer enough. Continuous external infrastructure penetration testing ensures that your perimeter security is consistently validated, helping to prevent breaches and reduce risk.
We can include any system that is exposed to the internet in the scope for an external infrastructure penetration test, including web applications, email servers, VPN gateways, DNS servers, firewalls, and cloud infrastructure. The testing focuses on the systems that could serve as an entry point for attackers.
Yes you will receive a report, however results (particularly high / critical findings) are communicated to you well in advance of that – often within hours of discovery. When you receive your report it will formally detail identified vulnerabilities, risk ratings, remediation guidance, and trends over time, helping you strengthen your security posture and demonstrate compliance.
Simply contact our security team to discuss your infrastructure, goals, and preferred testing schedule. We tailor our service to your environment and provide a clear roadmap for improving your external security.






