Cloud penetration testing from CREST certified testers
- Test cloud environments, infrastructure, applications, and services from AWS, Azure & Google
- Understand how a future successful attack could impact business operations
- Assure stakeholders, third-party suppliers, and customers that your cloud environments are secure
- Free retesting of issues found and no penalty fees if you need to re-schedule a test
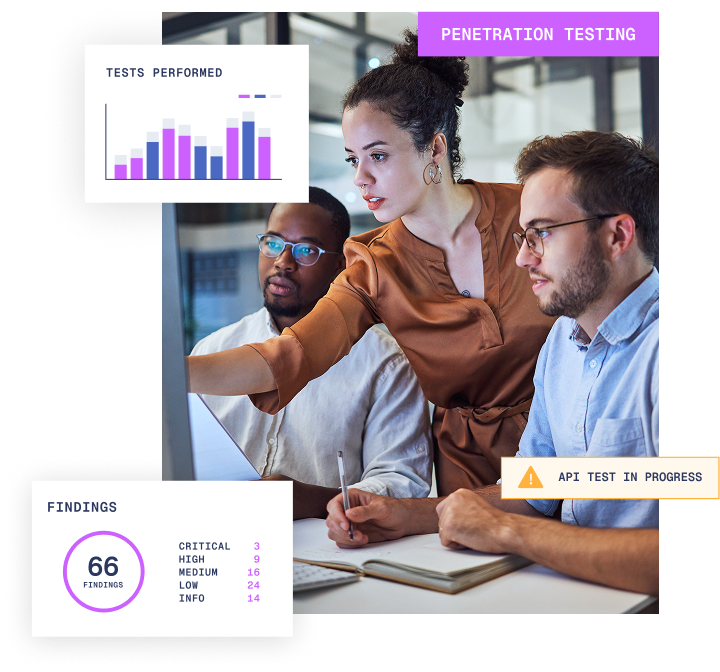
Get a faster, clearer, and simpler view of your cloud vulnerabilities
The cloud is where the future of business operations lies. While it brings agility, it also presents unique security challenges. With up to 80% of workers’ time now being spent in cloud environments it is essential you know it is secure.
Our cloud penetration testing will:
- Expose insecure functionality within your AWS, Google Cloud & Azure environments
- Uncover weak access controls to your cloud bucket storage
- Highlight vulnerable security perimeters in your cloud infrastructure
- Test and secure IaaS, PaaS and SaaS cloud deployments
- Secure the API’s and integrations that cloud apps rely so heavily on
Book your pen test scoping call
Ready to get a faster, clearer, and simpler view of your cloud security?
Whether you need help or a quote for a live project or just some quick advice, our team of cybersecurity experts here for you. Simply complete the form, or give us a call on 0330 460 4633 to start a conversation.
Trusted to provide a faster, clearer, and simpler view of cybersecurity by
What is involved in a cloud penetration test?
Our CREST certified penetration testers conduct manual and automated security assessments to simulate real-world attacks, while ensuring not impact day-to-day operations.
Configuration review
- A detailed review of your cloud configuration to surface mistakes and misconfigurations which are the most common source of exploitable vulnerabilities.
Advanced threat simulation
- We simulate advanced persistent threats to understand how your cloud infrastructure would withstand a cyber-attack.
Compliance assessments
- An evaluation your cloud environment against key industry standards including ISO 27001, GDPR, and PCI DSS to ensure compliance and reduce risk.
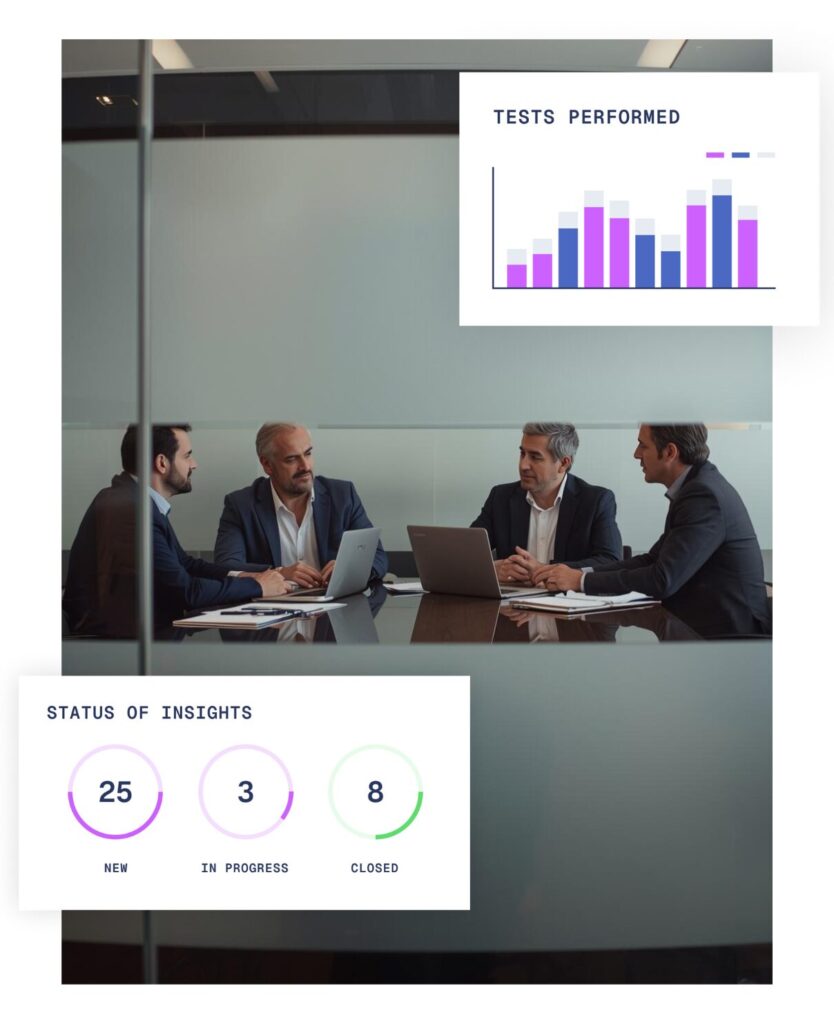
What you can expect from Vambrace penetration testing

CREST certified penetration testers
We use CREST certified professionals who bring extensive experience from across multiple sectors ensuring fast, accurate results.
Supported by our Aegis platform
Results from all pen testing activities are integrated into our Aegis risk management platform, automatically creating actionable and tracked task lists, prioritised by the most significant vulnerabilities, and aligned to your bespoke GRC requirements.

Access to immediate in-test reporting
No waiting for your final report. Our real-time reporting gives you live visibility of all findings as soon as they are submitted so you can start fixing critical issues fast. Post-test remediation checks ensure these vulnerabilities have been resolved.
A partner that is flexible to do business with
We get it. Businesses are busy, complex places, so if you need to move a start date, we will not charge a penalty fee.
Benefits of cloud penetration testing
Strengthen your organisations’ security posture
Early detection of vulnerabilities prevents data breaches, financial loss, and service disruption
Having a trusted third party assess your AWS, Google Cloud, or Azure environment is also an invaluable training and continuous improvement tool for internal teams as it:
- Provides actionable recommendations to fix vulnerabilities and improve security practices.
- Helps teams adopt better security controls, patch management, and monitoring practices.

Protect against wider cloud security flaws
AWS, Azure, and Google Cloud are highly customisable and one mistake can expose sensitive data. It is your responsibility to secure your organisation’s workloads in the cloud.
Misconfigurations occur when cloud services, resources, or settings are set up incorrectly, leaving systems vulnerable.
Insecure interfaces that interact with cloud services such as APIs and command-line tools are essential for managing cloud resources, but if they are not properly secured, attackers can exploit them.
The price of being popular: AWS, Azure, and Google Cloud are high profile targets and naturally attract high levels of attention from attackers. When it comes to publicly disclosed vulnerabilities, minutes matter. They are often communicated and tested against attacker targets very quickly.

Increase customer confidence
Customers will feel reassured knowing that your cloud environments have undergone rigorous testing to identify and fix vulnerabilities.
Use our Aegis platform to store and easily share all your cloud pen testing reports with your stakeholders. Having prepared documentation always available for inspection can significantly reduce deal closure and audit timelines.
Documented evidence of cloud security testing is either mandated or strongly recommended by most major security standards, especially when data storage, applications, and payment services reside there. Cloud penetration testing will help meet regulatory obligations against:
- PCI DSS
- ISO 27001
- GDPR
- HIPPA
- SOC 2
Cloud Penetration Testing FAQs
Cloud penetration testing is the process of evaluating the security of cloud-based applications, infrastructure, and services. It helps identify vulnerabilities such as misconfigurations, insecure APIs, weak authentication, and data exposure risks to ensure compliance and protection against cyber threats.
Cloud environments are highly dynamic and are often shared across multiple tenants. Without regular testing, businesses risk data breaches, unauthorised access, and regulatory non-compliance. Cloud security testing ensures your cloud setup is safe, resilient, and aligned with industry best practices.
Best practices include:
- After any major new project, feature releases or updates.
- At least once a quarter for ongoing security assurance.
- Whenever regulatory compliance requires it.
Yes, cloud penetration testing that is carefully planned and executed in a controlled manner will avoid disruption to your day-to-day operations.
You generally don’t need to notify AWS, Google Cloud or Azure for standard penetration tests against your own cloud environment. But you must respect their rules of engagement / acceptable use policies and avoid prohibited activities that could impact other tenants or the cloud infrastructure itself.






