Accelerate and simplify SOC 2 compliance
- Automatically generate custom policy templates and security procedures mapped to SOC 2
- Help and guide teams at every turn while returning up to 50% of their time
- Collect evidence, flag gaps, and implement fixes without relying on manual processes
- Get access to an experienced CISO level expert as standard
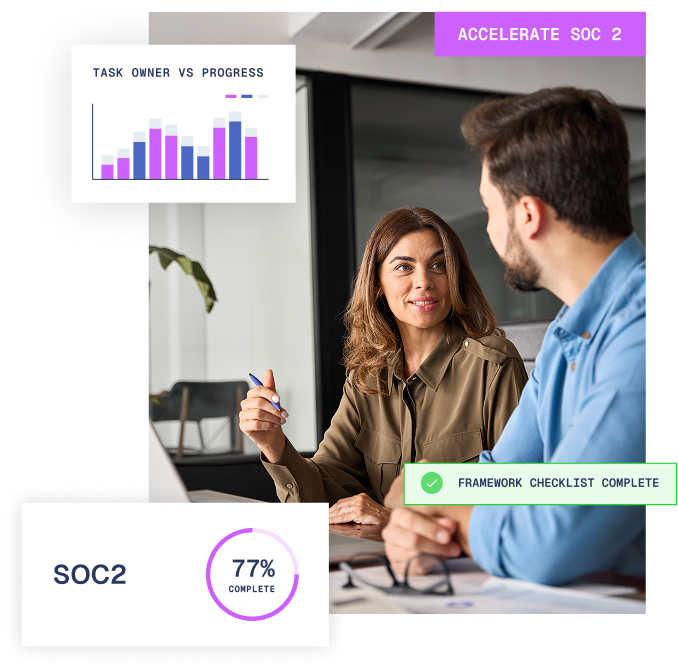
What you can expect from Vambrace
A full and fast SOC 2 compliance service, starting with automated gap analysis against the Trust Services Criteria to pinpoint where your organisation is falling short.
Aegis then automatically reviews evidence, flags gaps, and suggests fixes to help you get audit ready in weeks rather than months.
Speak to a SOC 2 expert
Ready to get a faster, clearer, and simpler view of SOC 2 compliance?
Whether you need help with a project, or just some quick advice, our team of experienced SOC 2 experts are here for you. Simply complete the form, or give us a call on 0330 460 4633 to start a conversation.
Trusted to provide a faster, clearer, and simpler view of cybersecurity by
Accelerate your SOC 2 compliance
With Aegis, the AI driven, automation powered platform that takes on the heavy lifting associated with SOC 2.
Automated evidence gathering, pre-populated documentation, and continuous monitoring will reduce discovery and setup time by up to 50% when compared to manual processes.
Aegis contains a comprehensive library of pre-written policies designed specifically for SOC 2, eliminating the need to author them from scratch.
- Aegis automatically cross-references existing evidence and controls already in place for other standards that can be used for SOC 2.
- Make the move from periodical checkbox to continuous compliance, where controls are monitored, measured, and maintained year-round.
- Instead of drafting multiple documents from scratch, Aegis automatically generates custom policy templates and security procedures mapped to SOC 2.
- Demonstrate and easily share your compliance achievements in the Aegis Evidence Hub for your auditors, clients, regulators, and prospects to view.
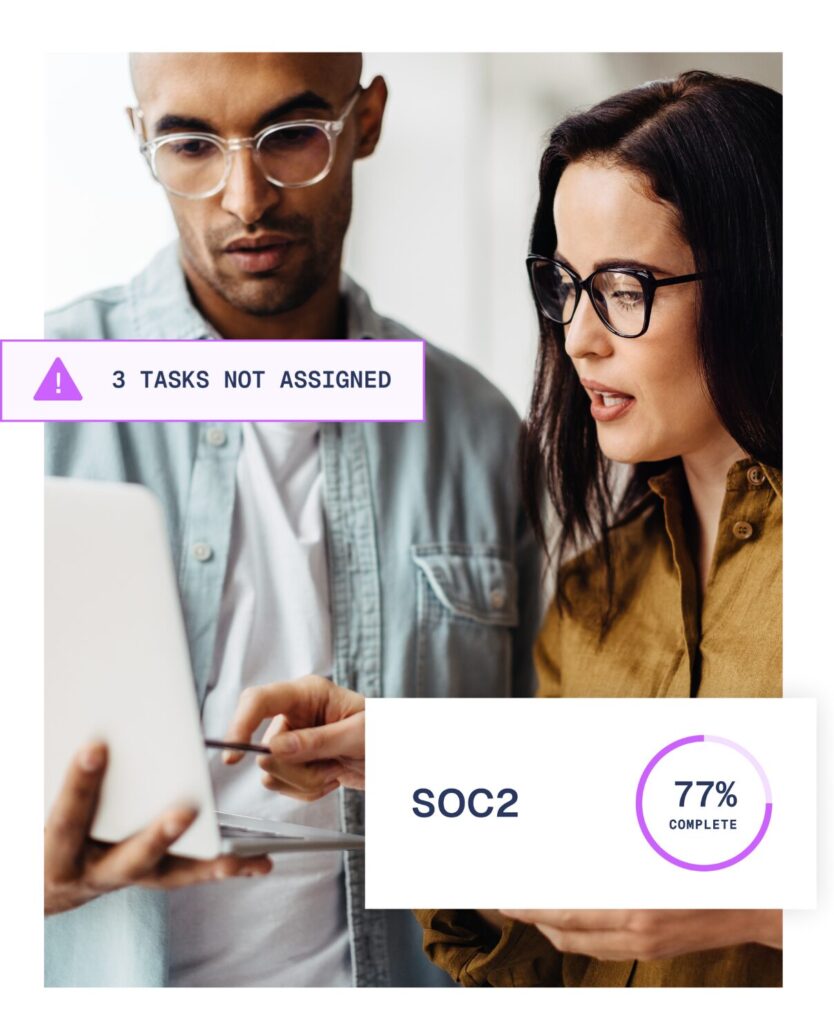
The role of your vCISO
All Aegis clients are assigned their own Virtual CISO (vCISO) as standard.
This experienced cybersecurity and compliance leader will be the main point of contact throughout our relationship and will lead the SOC 2 compliance process.
A vCISO takes the risk out of a high-cost hire. Full time CISOs are expensive but the truth is while all organisations need cybersecurity leadership to oversee security strategy and compliance, most do not need to pay for it on a full-time basis.
Get a head start with pre-written policies
Your vCISO will use Aegis’ comprehensive library of pre-written policies designed specifically for SOC 2, eliminating the need to author them from scratch. Covering the five trust services criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy, these templates establish and evidence a clear, auditable control environment.

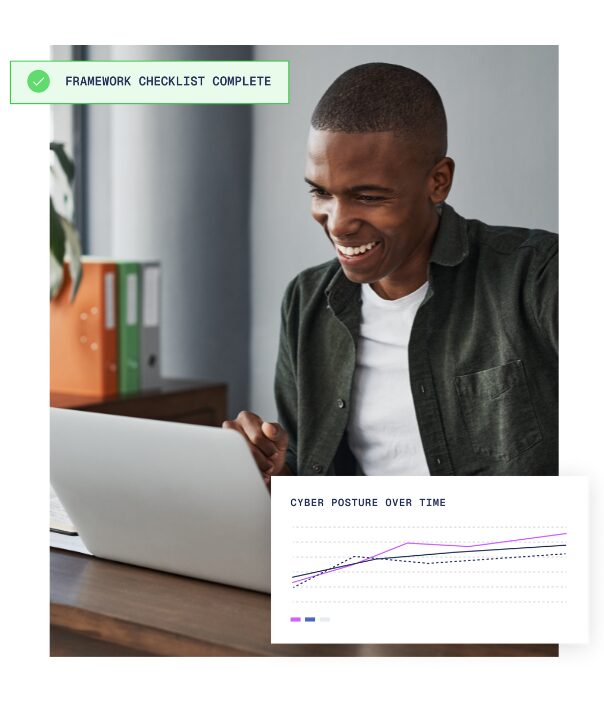
Be ISO 27001 compliant every day, not just on audit day.
Achieving ongoing SOC 2 compliance is about maintaining the controls and processes that meet the Trust Services Criteria continuously.
For this automation is essential. The last thing leaders need is for new issues to surface close to a re-certification date, resulting in costly delays. Aegis continuously monitors your systems, immediately flagging issues, and generating remediation snippets so teams can resolve failing areas fast.
What our customers say
Reasons to accelerate SOC 2 compliance
Reduce the risk of a data breach
Protecting sensitive data should be a high priority for any organisation, and the issue of a SOC 2 report demonstrates the implementation and maintenance of strong controls around data security.
By implementing the Security Trust Criterion, which is required for all SOC 2 reports, you lower the risk of a data breach, and all the possible impacts that brings, from ransomware and loss of operational control to regulatory fines.
Win more business
A successful SOC 2 audit will result in your organisation receiving a SOC 2 report.
Organisations are demanding to see evidence of stringent cybersecurity measures in place before agreeing to do business. According to the A-LIGN 2024 Compliance Benchmark report, 34% of organisations have reported losing business due to a missing certification.
Your SOC 2 report can be easily shared via the Aegis Evidence Hub with regulators and auditors, as well as prospective and existing customers.
Reduce costs
SOC 2 compliance can reduce your costs, and many organisations will see a positive ROI from the time and resources invested in it due to:
- Reduced cyber insurance premiums thanks to your now demonstrable risk management practices.
- Fewer security incidents mean less time and money is spent on remediation.
- Operations becoming more efficient thanks to standardised processes.
SOC 2 compliance FAQs
SOC 2 (System and Organisation Controls 2) is a framework developed by the AICPA for managing customer data based on five “Trust Services Criteria”: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
While not a legal requirement, SOC 2 compliance is considered essential for SaaS and cloud service providers, FinTech, HealthTech, data analytics companies, and any other organisation that stores or processes sensitive customer data. It is often a requirement for doing business with clients or operating in regulated industries.
- SOC 2 Type I: Evaluates controls at a specific point in time.
- SOC 2 Type II: Assesses how effective those controls are over a period of time (from 3 to 12 months).
Most organisations aim for SOC 2 Type II as it carries more weight with customers and partners.
There are five SOC 2 Trust Services Criteria, which must all be met to achieve a successful audit.
- Security – Protection against unauthorised access.
- Availability – System uptime and reliability.
- Processing Integrity – Accurate and timely data processing.
- Confidentiality – Protection of sensitive information.
- Privacy – Proper collection, use, and retention of personal data
It depends on your business goals and your customer base. If you operate in the U.S, deal with U.S based companies, or wish to deal with them in the future then it is likely they will expect a SOC 2 Type II report as part of their vendor security review. ISO 27001 alone might not satisfy them, especially in SaaS, service, or technology industries.
Having both ISO 27001 and SOC 2 can streamline security reviews and help expedite due diligence to close deals faster. ISO 27001 may suffice if you don’t handle much customer data or work in an environment with zero U.S exposure.
A SOC 2 report is valid for 12 months from the end of the audit period. At this point the report may be considered ‘stale’ by some customers and their procurement teams. To maintain trust and sales momentum, it is recommended to undergo a SOC 2 audit every year.







