Cybersecurity incident response | IR
Enlist an elite and experienced cyber incident response team who deliver a clear, calm, and trusted service when it really matters
- A full-service covering cyber incident planning, response, containment, and recovery
- Rely on a team with experience against every type of cyber-attack
- Our tailored plans and playbooks enable clear communication when it matters most
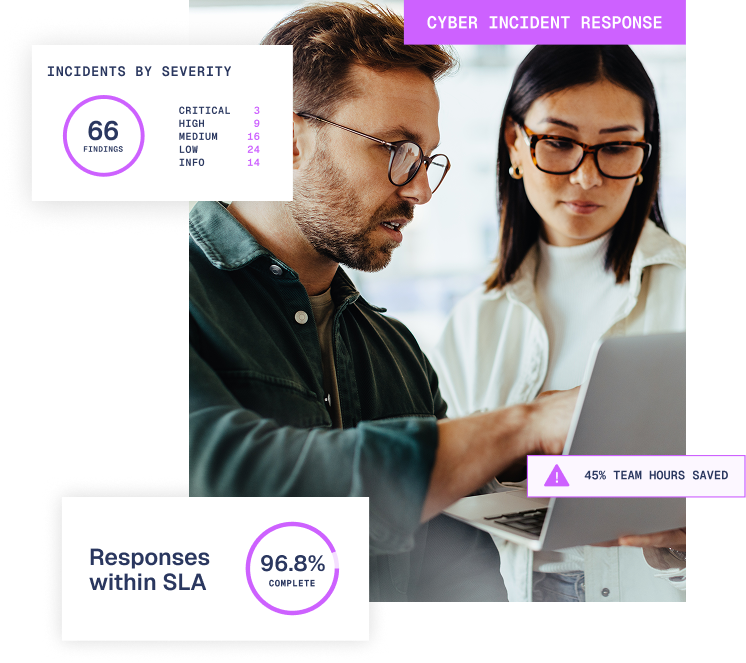
What you can expect from Vambrace
Proactive incident planning
Our team help you prepare by forming and testing proven, highly effective incident response plans and simulated scenarios based on the latest threat intelligence to reduce the impact of an attack and meet regulatory standards.
Rapid incident response
When an attack hits, our top priority is to stabilise the crisis fast by understanding what has happened as we move to protect and restore critical systems.
Post incident forensics and restoration
Our detailed sweeps across multiple environments show how attackers bypassed defences while surfacing hidden and dormant implants used for follow-up attacks.
Speak to a cyber incident response expert
Ready to improve your incident response capabilities?
Whether you need to start planning, run a table top or live play scenario, are currently experiencing an incident, or need help with post incident forensics our team of experienced cybersecurity experts here for you. Simply complete the form, or give us a call on 0330 460 4633 to start a conversation.
Preparation: The difference between a successfully contained incident and catastrophic breach
The first time a cyber incident response plan is tried out should not be on the day of an attack. Our team thoroughly prepares organisations by testing the effectiveness of planning, the clarity of policies, and robustness of communication channels through:
Tabletop exercises:
Discussion-based sessions that focus on team roles, responsibilities, communication, and priorities in line with the organisation’s cyber incident response plan for pre-agreed scenarios.
Ideal for Organisations:
- Early in their incident response maturity and need to validate plans on paper before progressing to technical drills.
- With distributed leadership that need to experience decision-making under pressure.
- Operating in heavily regulated sectors where compliance and communication strategies are as important as technical actions.
- With proactive teams who want to identify gaps in policies, escalation paths, and communications without disrupting live systems.
Live play scenarios:
Real-time sessions where participants execute their roles in response to controlled feeds of information representing a pre-agreed scenario, providing an in-depth validation of plans.
Ideal for Organisations:
- Who have existing security operations capabilities in house (such as a SOC, IR teams, and forensic analysts).
- Who maintain dedicated test environments where attacks can be safely simulated.
- Who need to validate technical detection and response capabilities (EDR, SIEM, log analysis, and containment workflows) on a regular basis.
- With proactive teams who understand the need to stress-test integrations between security tools, threat intel feeds, and automated response playbooks.
The Vambrace difference during an attack
The importance of a clear, pre-agreed protection retainer
The first few hours of a cyber-attack are critical. It should not be the trigger to start searching for an incident responder or creating response plans.
Vambrace’s Incident Response Retainer ensures you are always prepared with immediate access to elite responders working to pre-agreed playbooks and communication pathways within an agreed timeframe, with no red tape.
These retainer hours are flexible. Any not used can be applied towards other proactive managed security and intelligence services.
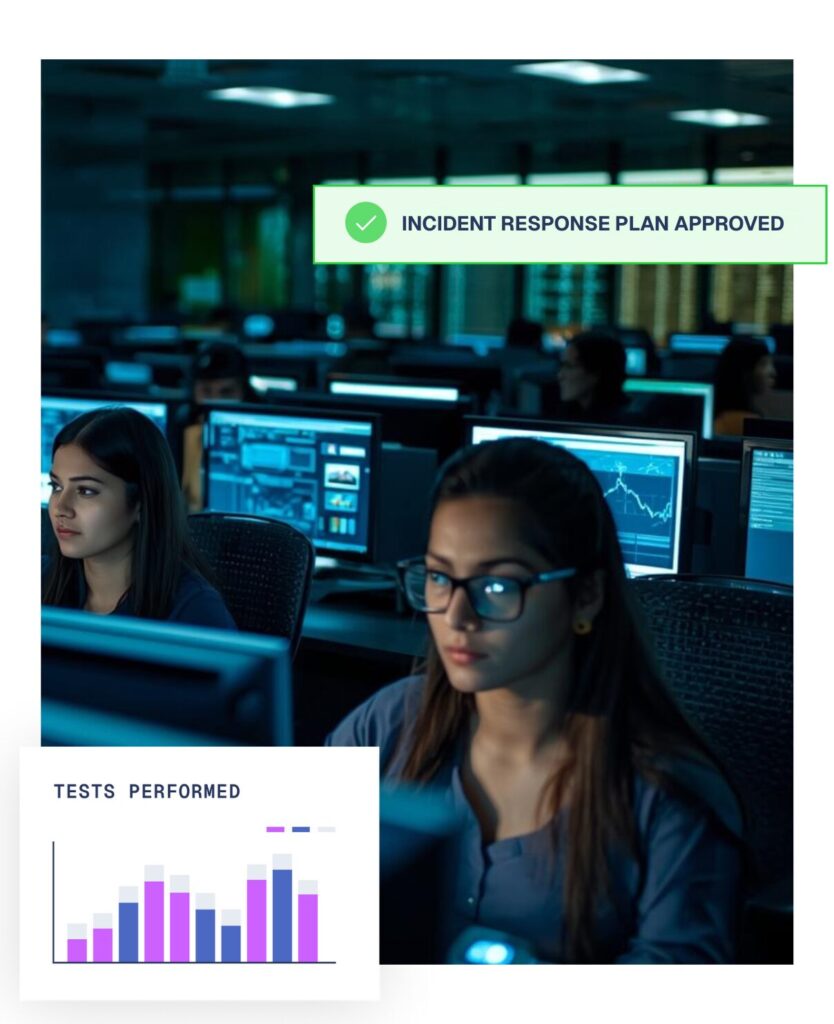
A focus on rapid response and containment
Our team leverages AI to enrich data, drive intelligence, and identify patterns in attacker tactics to accelerate investigations.
Our incident responders are available 24 / 7. When an attack hits, their top priority is to stabilise the crisis fast by understanding what has happened as they move to protect and restore critical systems.
Their work is supported by experts in our SIEM and SOAR operations, CISO level consultants, and Threat Intelligence analysts to ensure they are working with the very latest information.

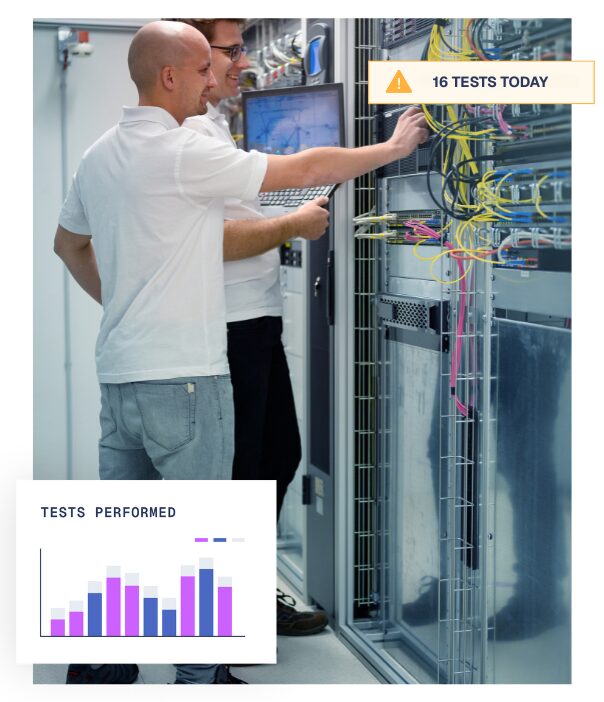
Post incident remediation and forensics
A full incident remediation service
Our team of forensic investigators and IT infrastructure engineers will work tirelessly to ensure you can return to ‘business as usual’ as soon as possible.
Forensic investigators remove adversaries from your environment, including hidden or dormant implants that could be used to initiate future follow-up attacks. They are expert evidence preservers, always working with copies and maintaining a clear chain of custody to preserve integrity.
Meanwhile, our infrastructure engineers will stay with you to assist with the reconstruction and recovery of critical systems and data, the upgrading of infrastructure, and strengthening of security posture for improved protection and resilience.
Learn more about Vambrace’s managed cybersecurity solutions
Cyber incident response FAQs section
A cyber incident response (IR) Team is a group of trained specialists responsible for managing and remediating a cybersecurity incident. Their role is to protect the organisation by minimising damage, restoring normal operations quickly, and preventing future attacks.
A cyber incident response plan (IRP) is a structured set of guidelines that outlines how an organisation detects, responds to, and recovers from cybersecurity incidents. It serves as a playbook for managing cyber threats, ensuring that response efforts are consistent, efficient, and effective.
An (IRP) is essential because cyber incidents are no longer a matter of if but when. Without a structured plan, organisations will waste precious hours they do not have and risk longer downtime, higher recovery costs, regulatory penalties, and lasting reputational damage. An IRP ensures your team can act quickly, consistently, and effectively when an attack occurs.
The key to effective incident response is preparation and coordination. An organisation must have clear processes, trained people, and the right tools in place before a cyber incident occurs. When a threat emerges, success depends on how quickly and effectively teams can work together to contain and remediate it.
Organisations choose managed cyber incident response services because they provide rapid access to specialised expertise, tools, and 24/7 support that many businesses cannot maintain internally. Cyber incidents are high-stakes events where minutes matter, and managed services help reduce downtime, financial losses, and reputational damage.
Key reasons include:
- Around-the-clock coverage – Threats don’t follow business hours, but managed teams monitor and respond 24 / 7.
- Specialised expertise – Providers like Vambrace bring advanced forensic analysis and threat intelligence skills that may not exist in-house.
- Scalability – Managed teams can quickly scale resources to match the size and severity of an incident.
- Regulatory and legal support – Providers like Vambrace are experienced in and will help the affected organisations preserve evidence, generate reports, and meet legal and compliance requirements.
- Cost efficiency – Outsourcing can be more affordable than building and maintaining a large dedicated internal team.
- Support for cyber insurance – Many insurers prefer (or require) the use of managed incident response providers to streamline claims.

