Cyber Maturity Assessment | CMA
- A comprehensive review of your cybersecurity posture with a focus on governance, risk, resilience, and incident response capabilities
- Mapped industry specific threat intelligence to existing priorities to ensure the best use of your resources
- Understand your organisation’s true ability to protect its data, IP, and people
- Your CMA will be conducted by an experienced CISO level consultant
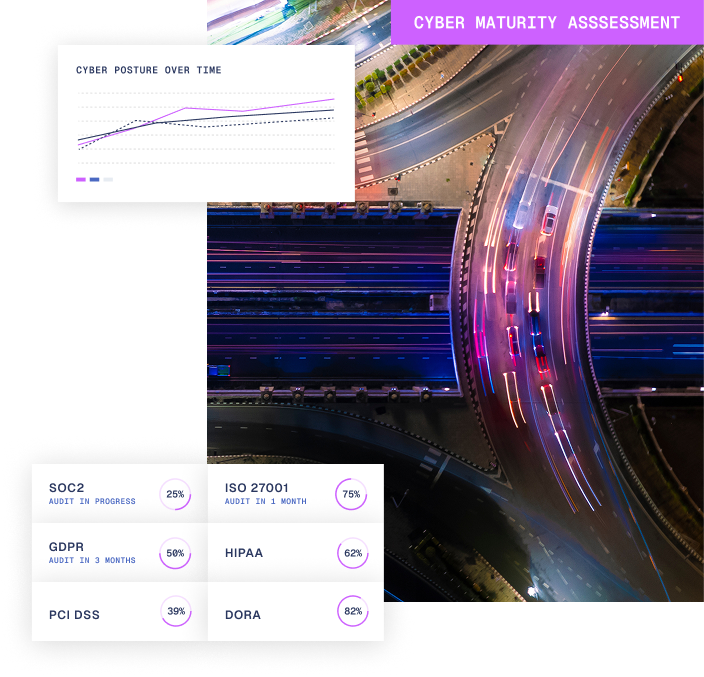
In today’s landscape cyber risk is business risk.
Yet many organisations are still making decisions with incomplete visibility, inconsistent controls, and poor intelligence.
Our Cyber Maturity Assessment (CMA) provides a practical, evidence-based picture of how well your people, processes and technology are working together to manage perhaps the greatest risk modern businesses face, and provides a clear roadmap on how and where to improve.
Speak to a CISO level expert
Identify issues early, before they become expensive headaches with a Cyber Maturity Assessment
Your CMA will be conducted by one of our experienced CISO level consultants, with their report aligned to your organisations security strategy and presented in plain English for your leadership team. Complete the form to start a conversation or give us a call on 0330 460 4633
Trusted to provide a faster, clearer, and simpler view of cybersecurity by
A Cyber Maturity assessment (CMA) is needed when
Executive teams require concise, risk-focused briefings
Security leaders are planning budgets or justifying investments

IT teams are preparing for audit, regulatory review, or third-party due diligence
Organisations are scaling quickly and need repeatable, reliable security
The Vambrace Cyber Maturity Assessment Framework
Your CMA can cover the entire organisation or specific departments or locations. We use an easy to understand five-level maturity framework that’s easy to digest and communicate across different teams. It also maps to key standards like NIST CSF, ISO 27001 and SOC2, helping to align to key compliance requirements.
Level 1 – Only ad hoc or reactive security practices are in place. For example:
- Controls are largely informal, undocumented, and dependent on individual or manual effort.
- Limited accountability or measurement.
- Security incidents handled on a case-by-case basis without consistent documentation.
Level 2 – Basic processes exist, but are inconsistently applied and often reactive. For example:
- Controls that are in place have not been adopted across the whole organisation.
- Patch management / scanning is performed regularly for some systems but not tracked or validated across the environment.
- There is a lack of experienced governance, risk, and compliance leadership.
Level 3 – Policies and procedures are standardised, documented, repeatable, and communicated across teams. For example:
- Clear evidence of reviews into access controls and privileges.
- Regular scanning in place with tracked remediation.
- Compliance with key information security frameworks can be evidenced.
Level 4 – Security processes are proactive, measured, and integrated into broader business management. For example:
- Data and metrics drive continuous risk reduction and accountability.
- Experienced CISO level led governance is in place.
- Incident trends are tracked over time and lessons learned incorporated into security posture.
Level 5 – Security is embedded into the organisations DNA. For example:
- Strong evidence of continuous improvement.
- Automation is being used effectively to help and accelerate tasks, reduce error, and enhance human expertise.
- Intelligence driven decision making with reliable, up-to-date, and accurate data is the norm.
The benefits of a Vambrace Cyber Maturity Assessment
Protect your bottom line
The goal of every Vambrace CMA is simple: To help the board protect the bottom line for the next financial year and beyond.
A CMA isn’t just about compliance, it’s a business tool that helps safeguard profitability by reducing cybersecurity risk. By identifying weaknesses before they become costly incidents, it ensures that your organisation’s security investments are delivering real value.
Ensures the best use of your resources
Not every security gap can be closed and vulnerability remediated. A CMA will give you the visibility of which are the most critical based on real-time data, so you can allocate resources accordingly.
- Prioritise high-impact improvements
- Align spending with risk appetite
- Enable data driven budgeting and reporting
- Support long term strategic planning
Get multi-dimensional, benchmark driven insight
We assess cyber maturity across people, process, and technology, and tie them to measurable business outcomes such as compliance coverage, downtime, incident containment, or your own bespoke metrics.
Our scoring criteria is informed by industry averages and best practices, allowing for meaningful comparisons to your industry peers and your key compliance standards.
Cyber Maturity Assessment FAQs
A cyber maturity assessment is a structured evaluation that measures how effectively an organisation manages and protects its data, IP, and assets. It examines the people, processes, and technology across key security domains to determine the current maturity level and identifies practical steps to strengthen resilience.
We measure maturity on a five-level scale, from Level 1 (poor) to Level 5 (Excellent). Each level reflects how consistent, repeatable, and proactive your security practices are. The result is a maturity score and roadmap showing exactly where to focus for maximum impact.
The timeline depends on the organisations size and complexity, but for organisations of between 1,000 – 4,000 employees, you can work on around 10 days plus reporting and debriefing time.
We don’t just leave you with a report. Your vCISO will walk you through the findings, explain the implications, and help prioritise next steps. You’ll get a custom improvement roadmap and the option for ongoing support to track your progress.
We recommend performing a maturity assessment annually or after major organisational or infrastructure changes (e.g. an acquisition). Regular assessments help track progress and demonstrate continuous improvement.
Yes. Our assessment methodology aligns with globally recognised frameworks including NIST Cybersecurity Framework (CSF), ISO 27001, CIS Controls, and Cyber Essentials. This means your maturity results can support or feed directly into certification efforts.






