Embedded Application Security | OpenGates
- Secure apps that run within your collaboration platforms like Microsoft Teams and Slack
- Identify misconfigurations, insecure patterns, or poor maintenance by vendors
- Generate audit-ready evidence for key compliance and regulatory frameworks
- See the value with a FREE initial report without giving us access to your M365 environment
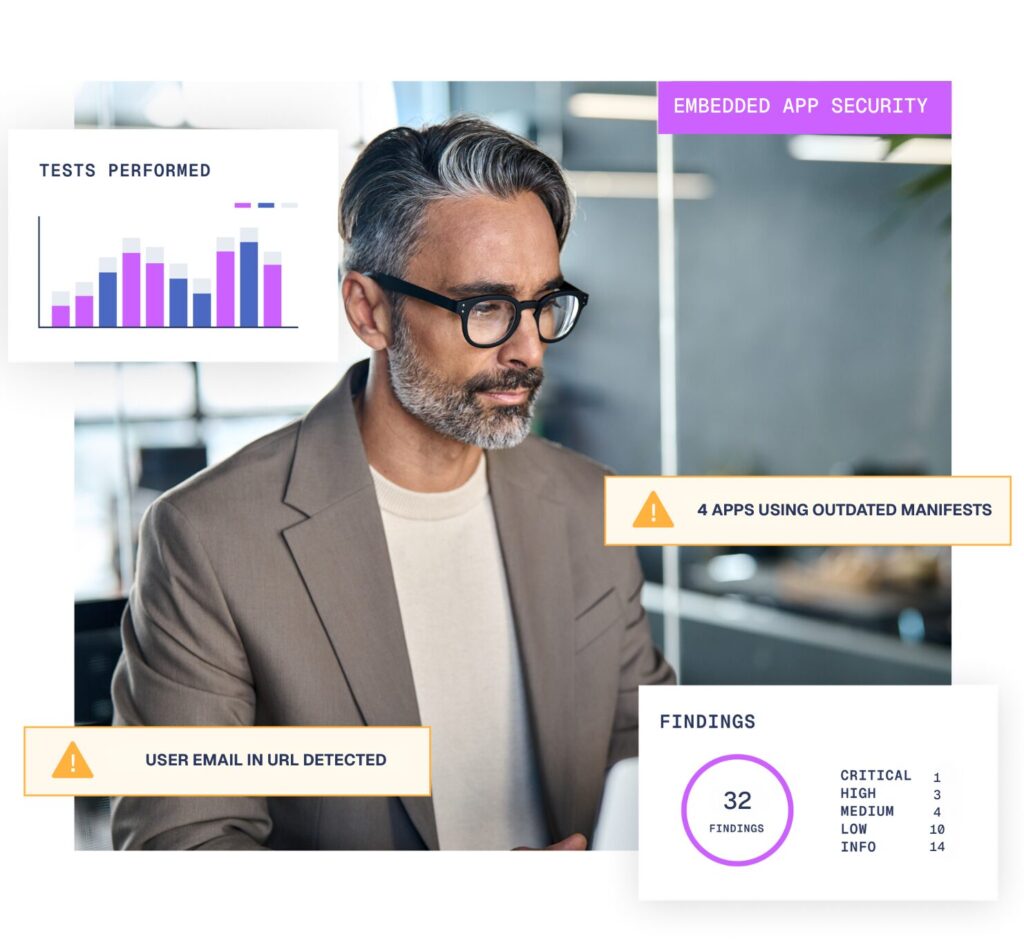
Embedded apps are quietly and quickly expanding attack surfaces
Embedded applications have become…well…embedded within our daily working life. Running
inside host collaboration platforms like Microsoft Teams and Slack, you will know them under their brand names. The project management tool Trello and communications platform 3CX are two prime examples.
The reason embedded app security should be stealing your attention right now is because they are quietly and quickly expanding attack surfaces for four very good reasons:
Speak to an embedded application security expert
Ready to get a faster, clearer, and simpler view of your embedded application security?
Whether you need help with a project, or just some quick advice, our team of experienced security experts are here for you. Simply complete the form, or give us a call on 0330 460 4633 to start a conversation.
Why embedded applications are expanding attack surfaces
Embedded applications are central to business operations. They drive productivity, save time, and improve communication. Without them functions like customer service, payments, and logistics would all suffer. But while companies race to integrate their own or adopt the latest third-party apps into their environment, security is often overlooked. This is where embedded application security comes in.
They are an attractive proposition to users
These apps are well designed and incredibly helpful, saving many people many hours across their working week.

They are very well and heavily marketed
Combined with the power of word-of-mouth means they can build a large following and user count very quickly.
They can be installed easily by users
With little friction and no cost for installation, security teams often find themselves unaware of their existence.
They will play by their own rules
Embedded applications will bring their own authentication, demand their own permissions, and call their own domains.
Trusted to provide a faster, clearer, and simpler view of cybersecurity by
The OpenGates platform
How Vambrace provides embedded application security for Microsoft Teams and Slack
Every new embedded app installation means a new set of data pathways and new permissions being requested, yet because of the frictionless installation process, security teams are often completely blind to them. Even mid sized organisations can have dozens of embedded applications.
OpenGates ingests and evaluates app manifests (the apps’ origins and rule book) and informs security teams with actionable insight into the permissions an embedded app is asking for, the external domains it calls, and how it plans to operate. We take this rule book and apply a layered risk assessment, which crucially can be applied at scale and covers:
- Manifest and configuration analysis
- Evidence of insecure data handling
- Permission scope alignment
- Continuous monitoring

The value of embedded application security
Most organisations are still in the very early stages of understanding just how significant the real-world threats are from these small embedded applications.
The risks OpenGates detects typically come from misconfiguration, neglected vendor components, and poor data handling, rather than malicious behaviours or sophisticated zero days attacks.
While we cannot block installation directly, with thousands of embedded apps now available, automated monitoring is now essential. OpenGates surfaces issues far quicker than any manual process could ever achieve, supporting policy guidance, and oversight to prevent potential attackers from leveraging embedded applications in the future.
How to get started with OpenGates
To arrange an OpenGates demo complete our form and a member of the team will be in touch very soon. Once the demo is complete we can also offer a FREE proof on concept (POC) that looks at a broad cross section of your current embedded applications with no need to provide us with access to your M365 environment, or even spend time on a scoping call.

What our customers say
Embedded Application Security FAQs
Embedded apps running inside Microsoft Teams rely on a complex blend of APIs, permissions, identity frameworks, and third-party services. Even when the host platform is secure, the app itself can introduce vulnerabilities such as insecure data handling, excessive permissions, API misconfigurations, and authentication weaknesses. Understanding these risks is essential because any flaw in the embedded app can expose sensitive business information, disrupt workflows, or become a stepping stone for attackers to access wider systems. A focused security assessment helps identify issues early, reduce exposure, and maintain compliance with internal and industry security requirements.
Yes. Platform approval does not guarantee that an embedded or integrated application is secure. Microsoft Teams, Slack, and similar platforms validate apps for basic compliance and operational functionality, but they do not perform deeper, assessments such as configuration analysis or permission scope alignment. Any custom code, API endpoints, authentication logic, data flow, and backend services remain your responsibility.
An embedded application security testing timeline depends on factors such as the number of apps in your Teams or Slack environment, their complexity, and integrations. For most environments, Vambrace can complete an assessment and issue the report within 48hours.
Costs are easily and quickly calculated based on the number of apps your organisation has enrolled. Factors such as app complexity, number of stores it is available on, and API integrations, have no bearing on the cost. With Mobstr there are no features available for a price premium. All our functionality is available to all customers.








