Attack Surface Management | ASM
View your network and supply chain from a hacker’s perspective in real-time.
- Continuously monitor and secure your entire attack surface with Aegis
- Surface crucial misconfigurations and vulnerabilities for key assets
- Deploy in any environment and start seeing results in minutes
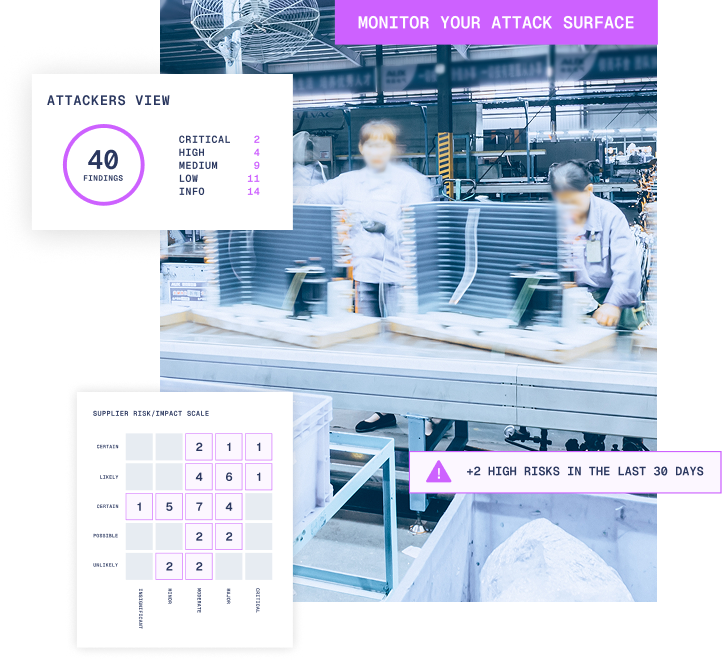
Take control of your entire attack surface
With increasingly interconnected supply chains, cloud infrastructure, and remote assets, attack surfaces are fluid and growing, making it difficult to maintain visibility.
Our Aegis platform is how leading organisations secure their attack surface. Aegis provides accurate, real time visibility into internet-facing assets, enabling continuous monitoring, discovery, and the prioritisation of fixing vulnerabilities within IT infrastructure.
Speak to an ASM expert
Ready to get a faster, clearer, and simpler view of your attack surface?
Whether you have a live project and need a competitive quote, or just some quick advice, our team of experienced experts are here for you. Simply complete the form, or give us a call on 0330 460 4633, and we’ll be in touch very soon.
Trusted to provide a faster, clearer, and simpler view of cybersecurity by
Continuous ASM with our Aegis Platform
How leading organisations gain visibility into and secure their attack surface.
You cannot protect what you do not know is there, and with attack surfaces rapidly increasing, AI driven automation is the only way for businesses to reliably and effectively continuously monitor for subdomains, login pages, API’s and other exposed services that could be leveraged by attackers.
Aegis recognises that not all vulnerabilities pose the same threat level, so it intelligently focuses on exploitable vulnerabilities that once remediated represent the greatest security gains and return on investment.
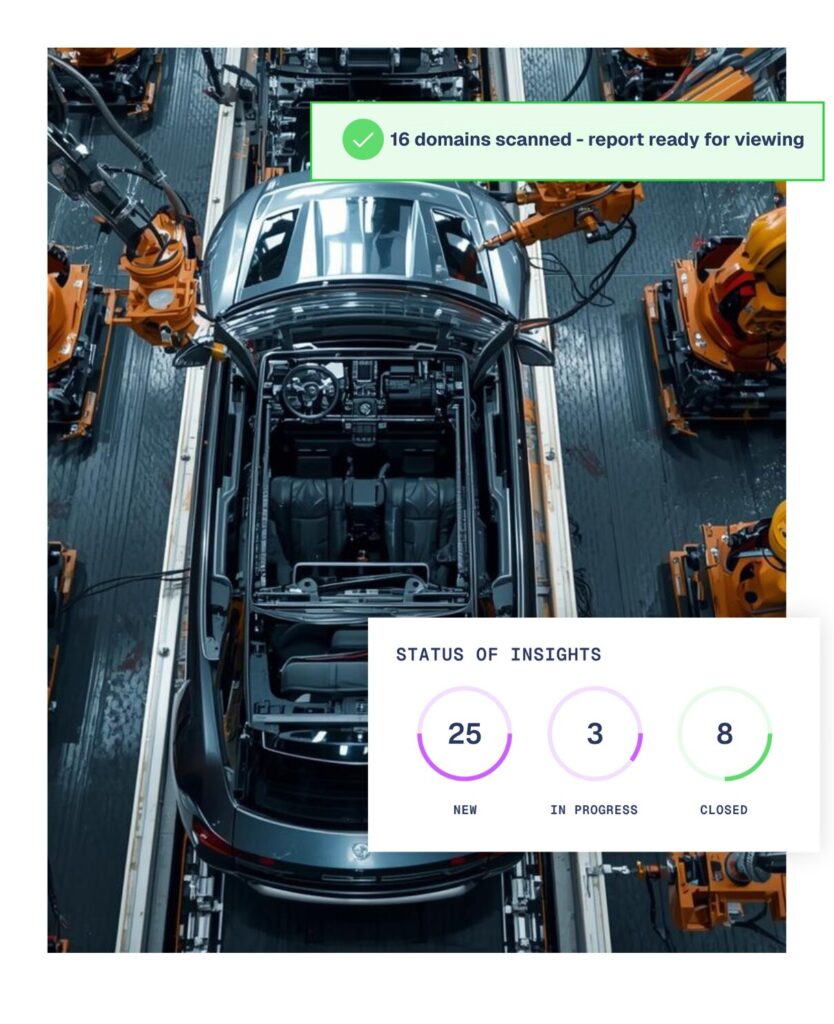
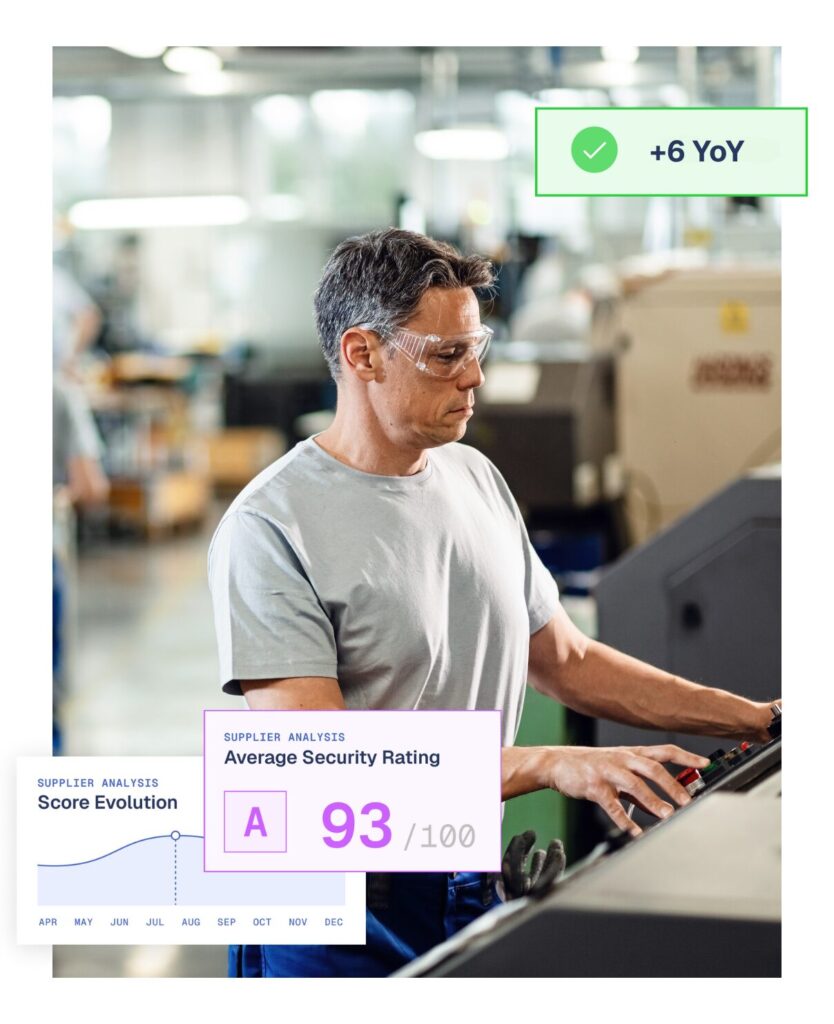
Aegis extends ASM to cover suppliers
Suppliers form a critical part of an attack surface – but do you know how secure they really are? Aegis will tell you.
Inheriting vulnerabilities from suppliers is a leading cause of cyber incidents. Aegis extends your attack surface visibility to assessing risks right across your supplier ecosystem with:
- Supplier security ratings that provides instant visibility into third-party security postures with risk scoring and compliance mapping.
- Automated risk assessments to continuously evaluate supplier risks throughout the relationship.
- Centralised risk dashboards that track and manage supplier risks from a single dash using built-in workflows for collaboration and remediation.
- Real time alerting to incidents that have the potential to change a key suppliers” risk profile, facilitating instant collaboration between teams.
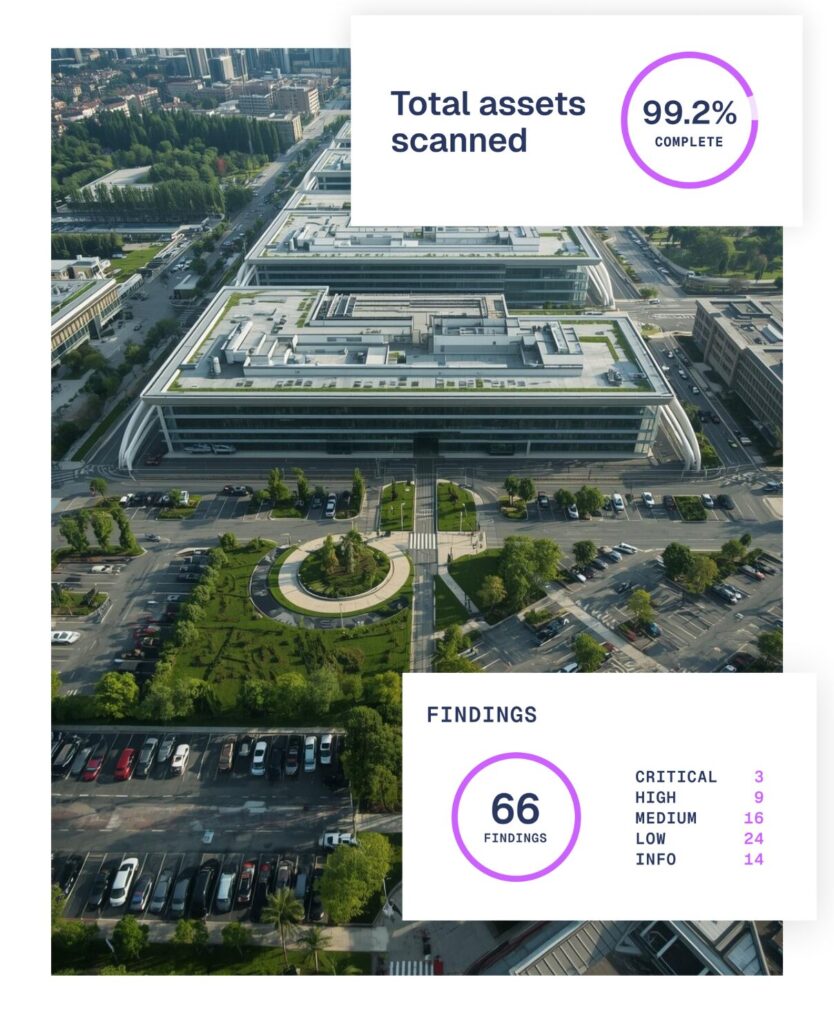
Aegis learns your attack surface
Map and document your internet facing assets, automatically prioritising those that pose the greatest risk to operations.
- When a previously unknown asset is surfaced, Aegis automatically assigns a risk rating and attribution to it.
- It will also highlight the assets weaknesses, including outdated software, open ports, weak SSL configs, and misconfigured APIs
- This process is perpetual. No manual intervention from your team is required.
Attack Surface Management FAQs
An attack surface is the total number of points where an attacker could try to gain access to your systems, applications, or data. This includes internet-facing assets, cloud services, APIs, endpoints, third-party tools, and even misconfigured or forgotten systems.
Attack Surface Management is the continuous process of identifying, mapping, monitoring, and securing all external-facing assets in your IT environment. It helps organisations uncover shadow IT, eliminate blind spots, and reduce risk by understanding what attackers see from the outside.
Mapping your attack surface gives your security team complete visibility into exposed assets and vulnerabilities. Without it, organisations risk leaving unknown, unmanaged, and unsupported assets exposed to attackers. By knowing your full attack surface, you can prioritise remediation, close gaps faster, and strengthen your overall cybersecurity posture.
Attack surfaces will change based on dozens of factors. Even for smaller organisations it has the potential to change daily as new assets are deployed, configurations shift, and employees adopt new tools. As a result, effective attack surface management is very much a perpetual task, not a one-time project.







